Get Rid Of Ransomware: The NetApp holistic approach to ransomware recovery
There are three stages in any ransomware attacks – before, during, and after. In the world of data protection, there is a lot of focus on the last stage, recovery, especially recovering encrypted virtual machines from backups.
Here comes our final stage of the Ransomware protection series Phase 3 – Recover.

This article will cover what happens after a ransomware attack. Hopefully, you are prepared to “detect” and “protect” an attack by following the necessary ransomware recovery steps. In this article, we will discuss the key steps to get you back online, minimize overall costs to your organization, reduce reputational damage, and alert the right people. With forensics data breaches and audits by Cloud Insights and ONTAP’s rapid recovery capabilities, we will focus on how you can recover in seconds.
What is ransomware recovery?
Ransomware data recovery is the process of bringing IT systems back online after a ransomware attack. Recovery can be simple, and it can follow many of the existing disaster recovery processes you have today, provided your disaster recovery plan is well documented and thoroughly tested.
In the event of a ransomware attack, an effective response plan makes all the differences. It determines whether the incident is controlled and quickly remediated, or escalates into a company-wide infection leading to a permanent shutdown.
Generally, people’s first reaction towards a ransomware attack may be to restore their data immediately. But the point is, if you want to prevent reinfection and not waste your precious time, you must take extra steps to make sure the ransomware doesn’t come back. Therefore, here are three steps to remediate your environment from ransomware infection with NetApp ONTAP.
Three effective steps NetApp remediate your environment properly and holistically from ransomware infection.

Ransomware Recovery Step 1— Contain/Isolate
Let’s look at the whole ransomware process step by step. It usually starts with mistakenly clicking on malicious links, leading to the installation of ransomware. And guess what – This always happens on the client’s side! After ransomware installation, the ransomware will encrypt the local file system, then continue to spread to any file share it can find throughout the network.
To contain the outbreak, you must identify and isolate infected clients by disconnecting them from the network.
To achieve this, we suggest the ONTAP for SMB shares with two CLI options that can be used for monitoring access to an NFS share on an ONTAP system. In order to clean up the infection and move to the next step, it is recommended that you use antivirus and antimalware software to clean up after a ransomware attack. Read more on Microsoft Management Console (MMC) plug-in with ONTAP for SMB shares and Using Windows MMC with ONTAP.

Ransomware Recovery Step 2— Prepare/Patch
Preparation is crucial. After being clicked by the client, a typical ransomware uses known vulnerabilities to get itself installed and starts causing repeating issues. Patches are often available for these vulnerabilities, but software patches have not yet been applied to client computers. However, many systems remain unpatched. In this preparation phase, the key is to remove and clean the infection and patch the client as soon as the vulnerability is discovered, and a patch is available.
If you disconnect and clean infected clients, but not patch them, the client system would most likely be re-infected with the same ransomware very quickly. Therefore, it is critical to remove and clean the infection and patch the client once a vulnerability is discovered and a patch is available.
After you make sure steps 1 and 2 are run in parallel, the client machines will be cleaned and patched. It is likely that systems will not be reinfected by the same ransomware. You can put them back on the network and it will take you back to where you were before the infection.
Ransomware Recovery Step 3— Recover/Restore
The last step is to recover your data that has not yet been infected.
The final step is to recover data that has not yet been infected. You may choose to perform this step earlier if you want to quickly get your data back online.
For example, if encrypted data is critical to your business operations and if you can quickly isolate all infected clients from the network, it might make sense to restore data as soon as possible before cleaning and patching those clients.
Normally, during this recovery step, clients need to identify backups that are not infected by the ransomware, which is a time-consuming process However, if you use NetApp ONTAP Snapshot™ copies, you can skip the step of identifying ransomware-free backups, as all snapshots are read-only and immutable.
Ransomware Recovery: ONTAP recovery capabilities
After performing these three steps, you can recover your data safely and successfully.
While many other vendors offer copy-on-write snapshots, ONTAP Snapshot copies are read-only, immutable, and unaffected by ransomware. Therefore, all you need to do is restore the data upon ransomware attack, saving time from identifying an unaffected copy. Let’s take a look at the significant value that NetApp snapshots can provide compared to backup and recovery solutions from other vendors.
ONTAP Snapshot™ recovery in seconds
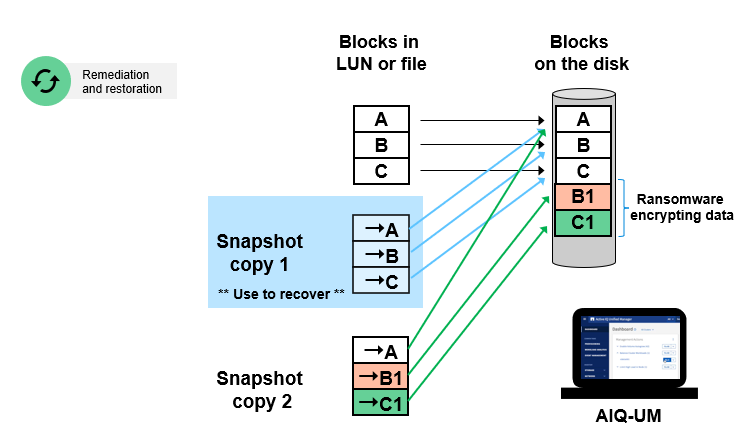
Everyone knows that the fastest way to recover from a ransomware attack is from a backup. It sounds simple, but the actual recovery process can be slow and complicated. The larger the amount of data encrypted in a ransomware attack, the longer the recovery process will take before you can regain access to all your data.
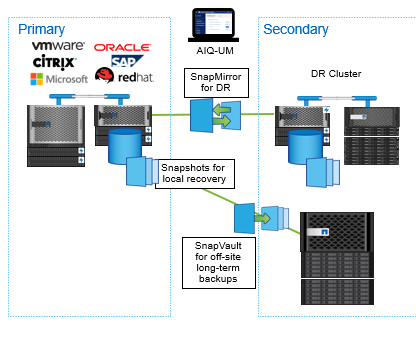
To avoid downtime costs caused by ransomware, you can leverage on the power of Snapshot copies across your ecosystem for disaster recovery, data archiving, and data tiering. ONTAP snapshot technology guarantees very low recover time as its file pointers can restore terabytes of data in seconds, delivering fast recovery.
This approach makes them ideal for fast recovery in NetApp file systems, providing you with tremendous value compared to backup and recovery solutions from other vendors. It also prevents valuable backup data from being deleted and protects your backups from ransomware encryption. For more information on the NetApp snapshot, please read Ransomware Protection: How would NetApp provide protection after ransomware being detected.
ONTAP Snapshot™ Resilient Retention Period
An appropriate snapshot retention policy is a value-added feature that you can employ when implementing snapshots to ensure that they are always available for recovery.
NetApp snapshots are read-only and cannot be infected by ransomware. However, you may want to make sure you keep a copy long enough to recover your data and avoid situations where ransomware is dormant. While the ransomware is hibernating, you may have deleted all snapshots because your snapshot retention period was not long enough and exceeds the recovery window. A proper snapshot retention policy allows you to keep snapshots for months (or longer) , rendering it more likely to recover from hibernating or slow-moving ransomware.
Controllable Snapshot Auto-Deletion
NetApp ONTAP allows you to turn off automatic snapshot deletion. Automatic deletion of snapshots should be a nice feature in the first place to prevent volumes from filling up all the time. However, during a ransomware attack, you would rather have a volume that is full but still contains a recoverable Snapshot copy. Controlled snapshot auto-deletion prevents snapshots from being automatically deleted.

NetApp SnapLock Provides WORM Immutable Storage
Even though NetApp ONTAP allows you to turn off automatic snapshot deletion, administrators can still delete them manually. This would expose snapshots to human error, such as malicious manipulation by a disgruntled employee, or hacker who steals credentials. This is where NetApp’s SnapLock® write-once, read-many (WORM) compliances solution comes into play. Once the file is written and committed to WORM state, it prevents changes to the file and makes the copy truly immutable. Please read our last article for more information on NetApp SnapLock®.
Active IQ Unified Manager — Ransomware protection best practices
NetApp Active IQ plays an important role in ransomware protection.
Active IQ Unified Manager prevents snapshots from being deleted by the system by setting the snapshot expiration time. In ransomware recovery, the ONTAP file system saves all encrypted data as well as the original unencrypted data in a Snapshot copy. This uses more storage space than normal, and the volume space starts to fill up. You can configure automatic volume resizing to increase volumes that are almost full to prevent them from filling up. Additionally, you can use thresholds to set alerts when volumes are nearly full to keep everything safe.
Not only does Active IQ close security breaches, but also provides insights and guidance on ransomware protection. There is a dedicated health card showing actions required and risks addressed, so you can be sure your system complies with these best practice recommendations. As you can clearly see, Active IQ ensures that your NetApp systems comply with best practices for fighting ransomware.
You may check out this on how NetApp Active IQ detects ransomware.
Conclusion : NetApp ONTAP® holistic approach to the whole ransomware recovery
It’s clear that ransomware is constantly evolving. Just as defense methods have improved, so have attack methods and vectors.
Using a portfolio of solutions that includes partners and third parties provides us with a layered defense. The NetApp solution differs from traditional solutions by providing a variety of effective ransomware recovery, ransomware detection, and ransomware recovery tools. Helps you understand, detect, and fix ransomware without costly downtime. Let’s review how NetApp ONTAP® provides an integrated approach to overall ransomware recovery.
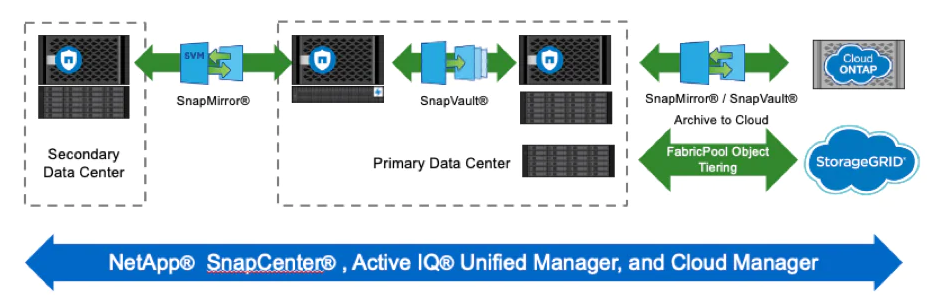
Storage: NetApp ONTAP
- NetApp Snapshot technology. A Snapshot copy is a read-only image of a volume that captures the state of a file system at a point in time. These copies don’t take up a lot of storage space. In the event of an attack, volumes can be rolled back using Snapshot copies taken before infection.
- NetApp FPolicy technology. When a file with a disallowed extension attempts an unauthorized operation, FPolicy would block the operation.
- NetApp SnapRestore technology. SnapRestore data recovery software is useful for recovering from data corruption or just recovering file contents. This efficient recovery process helps bring the business back online quickly.
- NetApp SnapLock technology. Files in SnapLock are stored in a non-erasable, non-rewritable state and cannot be deleted until the retention period expires. A user’s production data can be mirrored or stored to SnapLock volumes via NetApp SnapMirror or SnapVault technologies, respectively.
- NetApp SnapCenter technology. SnapCenter provides an easy-to-use enterprise platform to securely orchestrate and manage data protection across applications, databases, and file systems. It makes it easier and faster to restore applications to a consistent state.
About ATech Communication (HK ) Limited
ATech is a Leading IT service provider in Hong Kong. Do you want to learn how you can further protect your organization with ATech’s leading IT solution? Check out our IT solutions webpage or email our experts for a free consultation.
Ransomware FAQ
Ransomware is malicious software that encrypts the info of targeted victims. The attacker then demands the victim to pay a ransom for the decryption key.
Ransomware may be a multi-stage attack packaged by attackers in many various ways. The essential principles are usually equivalent. Infiltrate the target network, encrypt the maximum amount of data possible, and demand ransom. They are:
- Infection
- Secure Key Exchange
- Encryption
- Blackmail
- Unlock and restore
Regardless of the volume size or the level of activity on the NetApp storage system, creating a NetApp Snapshot copy only takes a few seconds, or even less than a second. Users can store up to 1023 Snapshot copies per WAFL volume, all of which are accessible as read-only and online versions of the data.
SnapCenter supports a variety of applications and protocols. Consult the NetApp Interoperability Matrix Tool (IMT) for details.
ONTAP® is the industry-leading enterprise data management software for NetApp storage.
ONTAP® helps you create a smart, powerful, and trusted storage infrastructure that reduces costs accelerate critical workloads, and protects and secures data across your hybrid cloud.
NetApp SnapLock software delivers high-performance disk-based data permanence for HDD and SSD deployments. It provides data integrity and retention, enabling electronic records to be both unalterable and rapidly accessible. SnapLock also integrates with top archive and enterprise content management (ECM) applications. It includes the ability to address an expanded set of retention requirements, including Legal Hold, Event-Based Retention, and Volume Append Mode (VAM). VAM allows customers to incrementally append files while locked for use cases such as video and audio surveillance and logging.
SnapLock provides fast WORM (Write Once, Read Many) storage which the high-performance, non-rewritable, non-erasable disk storage (SSD or HDD) helps protect data until a specified retention date. It supports disk-to-disk backup and replication of SnapLock volumes, as well as NDMP to tape. Its storage-efficient technology reduces the space required by archives and archive backups by 50% or more.

ATech Communication (HK) Limited
Providing a Complete Suite of IT Solutions
- (852) 2970 6010 / 3756 0078
- enquiry@atechcom.net


