Compliance and Security - NetApp
Data Management Technology – NetApp Products and Solution
Compliance and Security
- ONTAP Ransomware detection - SnapLock - Cloud Secure - Cloud Data Sense
Compliance and Security
Compliance and Security : SnapLock®
Compliance & Security
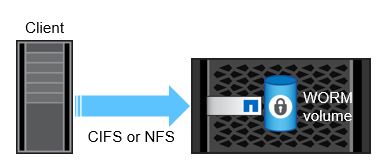
NetApp® SnapLock® volumes
Compliance volumes
(disk level protection)
and
Enterprise volumes
(file level protection)
Supported administration models
NetApp SnapLock
Compliance
and
SnapLock Enterprise
Certified data compliance
NetApp SnapLock is certified to meet stringent industry requirements, such as the SEC 17a-4(f) rule, FINRA, and CFTC.
Compliance & Security -
NetApp® SnapLock® Compliance
NetApp All Flash FAS, FAS
- Deployed for strict regulatory requirements such as SEC17a-4 and CFTC rule 1.31(b)
- Administrator is not trusted to perform delete operations
- All user and administrative operations are protected
- Aggregate rename now allowed (ONTAP 9.8 and later)
- Volume and aggregate deletion not allowed before expiration
- Zeroing disks and sanitizing not allowed
Compliance & Security – NetApp® SnapLock® Enterprise
Enterprise All Flash FAS, FAS, NetApp ONTAP Select
- Deployed for flexible regulatory requirements and organization-defined policies
- Administrator is trusted to perform delete operations (privileged delete)
- Administrative operations are
allowed (but securely recorded) - Volume and aggregate rename allowed
- Volume and aggregate deletion allowed before expiration
- Zeroing disks and sanitizing allowed
Compliance & Security : Cloud Secure

Cloud Secure Why Cloud Secure?
- Detect ransomware attacks before it’s too late
- Minimize the impact of an attack with automatic data backup
- Gain visibility into malicious user activity and identify potential policy risks
- Easily satisfy audit reporting requirements saving time & money
- Simple SaaS solution, quick time to value, no upgrades, scalable from single departments to global enterprises
How Cloud Secure Works?
Cloud Secure does not assume a trusted internal network, it takes a trust no one approach. It inspects and analyzes all data access activity in real-time to detect malicious behaviors.
Monitor User Activity
To accurately identify breaches, every user activity across on-premises and hybrid cloud environments, is captured and analyzed.
Detect Anomalies & Identify Potential Attacks
Cloud Secure uses advanced machine learning algorithms to uncover unusual data activity and detect a potential attack.
Automated Response Policies
Cloud Secure alerts you and automatically takes a data snapshot when detecting a risky behavior, making sure your data is backed-up and you can recover quickly.
Forensics and User Audit Reporting
Provides a graphical interface to cut and slice activity data to perform data breach investigations and generate User Data Access Audit reporting.
Compliance & Security : Cloud Data Sense
Empower Data Governance and Compliance Teams
Automate the inefficient processes that take weeks down to minutes
Ensure Sensitive Data Is Stored Where You Want It
Protect your IP and enforce restrictions on sensitive data
Stay Optimized, Save Money
Get an up-to-date view of what kind of data makes up the storage footprint
Maintain Constant Control
Maintain visibility of all sensitive data on systems to reduce the risk of privacy breaches.
Maintain Compliance
Get reports that prove your organization is compliant in seconds not weeks
Maintain
Governance
- View insights on redundant and stale data to optimize storage costs
- Understand what sensitive data is not secured
- Receive alerts if sensitive data needs attention
Demonstrate
Compliance
- Empowers enterprise storage and IT management teams to take control of data and deliver direct value in supporting data Compliance and Governance efforts in real-time and with no extra effort.
Automate Repetitive
Daily Tasks
- Run compliance reports instantly
- Share insights and information seamlessly.
- View up to date information on your storage footprint and what needs attention
- Turnaround ad-hoc requests for information in minutes not weeks
Cloud Data Sense - Benefits:

- Efficiency
- Eliminates manual and repetitive governance and compliance tasks
- Generate compliance reports in minutes not weeks
- Immediately identifies security risks and alerts you when potential risks need attention
- Locates all data on a certain subject with a click of a button
- Governance
- Maps all data
- See stats on sensitive and non-sensitive data
- Highlights redundancies for optimization opportunities
- Drilldowns for detailed insights
- Visibility
- See what sensitive data is not secured correctly for risk prevention
- Data is automatically classified and categorized based on its contents to easily identify what makes up the storage footprint
- Seamlessness
- Simply turn it on to get started and view dashboards instantly
Compliance & Security - ONTAP Ransomware detection
Compliance & Security
Get ready for Ransomware 2022, the state of ransomware at a glance
Ransomware 2022 – Data protection is part of Ransomware Protection! Ransomware attacks are part of the reality on the internet that you don’t have to …
Get Rid Of Ransomware: The NetApp Holistic Approach to Ransomware Recovery
Get Rid Of Ransomware: The NetApp holistic approach to ransomware recovery There are three stages in any ransomware attacks – before, during, and after. In …
Ransomware Protection: How would NetApp provide protection after ransomware being detected
Ransomware Protection: How would NetApp provide protection after ransomware being detected Ransomware is certainly not something new to you and your organization. You must have …
Ransomware attack? You are the next one!
Ransomware Attack? You are the NEXT ONE! There are $20 Billion damages from ransomware in 2021. Ransomware is the fastest-growing version of cybercrime, and it …
What is the best way to detect Ransomware?
detect ransomware Why detect Ransomware? Ransomware is the fastest-growing version of cybercrime and it is indeed that the downtime caused by ransomware is costly. There …
What is Ransomware and Why you can’t prevent it?
ransomware hk What is ransomware? Ransomware is malicious software that encrypts the info of targeted victims. The attacker then tried to urge the victim to …





