detect ransomware
Why detect Ransomware?
Ransomware is the fastest-growing version of cybercrime and it is indeed that the downtime caused by ransomware is costly. There is a new hourly metric for the downtime cost at $84,650 in ” Data Protection Report 2021“. The high reliance on applications and services means that any downtime is a threat to user productivity and can cause a significant loss of revenue. This is the reason why many organizations focus on a fast recovery. What if you could detect when the ransomware incident started and stop its spread?
The best way to combat ransomware is to implement a “detection, protection, and recovery” solution to determine data protection and security readiness. This means proactively identifying internal and external threats before actual attacks, protecting our data by preventing attraction and minimizing data loss or downtime, and restoring data applications as soon as possible after the attraction to help reduce data loss and interruption.

This blog is the second part of the series and discusses how to analyze and detect ransomware by NetApp Cloud Insights and NetApp® ONTAP® software. If you would like to learn more about the background of Ransomware, it is highly recommended you read ‘What is Ransomware and Why you can’t prevent it?’ here before you start reading this article.
More information:
Analyze and Detect Ransomware
ATech cooperates with the best data protection company — NetApp has become a long-term partner of Hong Kong. With NetApp, we help you to ‘Detect, Protect and Recover’. NetApp Cloud Insights and NetApp® ONTAP® software is the best combination to analyze and detect ransomware.’ So what they are and how can they help you? Let’s get to the details!
NetApp Cloud Insights
NetApp Cloud Insights (Cloud Secure) or external user behavior analysis (UBA)
- Identify the user file access patterns
- Identify possible end-user accounts become ransomware attack victims before the attacks intensified
- Detecting user exception
How Cloud Secure works
NetApp Cloud Insight is a risk analysis data access patterns to identify ransomware attacks. It reports from insiders, outsiders, ransomware attacks, and rogue access user activity. Identify the offenders and the possible threat becomes easy by advanced reporting and auditing. Moreover, Cloud Secure assuming that each person is zero trust instead of assuming a trusted internal network. That is really different from the perimeter security tools. Besides, it offers real-time monitoring of all activities and analyzes all data access to detect malicious behavior. Users are able to ensure compliance with regulatory requirements by audit all documents access.
Cloud Secure performs 4 main functions:
• Monitor user activity
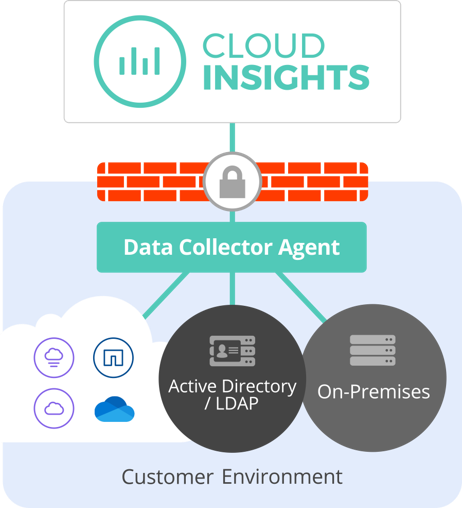
To accurately identify violations, the system will capture and analyze each user activity locally and in hybrid cloud environments. It used a lightweight stateless data collector agent installed on a VM in the customer’s environment to collect data. This data includes user data from Active Directory and LDAP servers, and users file activity from NetApp ONTAP®.
Cloud Secure by building a behavior model for each user to detect abnormal behavior of the user. The behavioral model detects abnormal changes in user activity and analyzes these behavioral patterns to identify threats to blackmail software, malware, or malicious users. Using this behavioral model can reduce false positives.
• Detect anomalies and identify potential attacks.
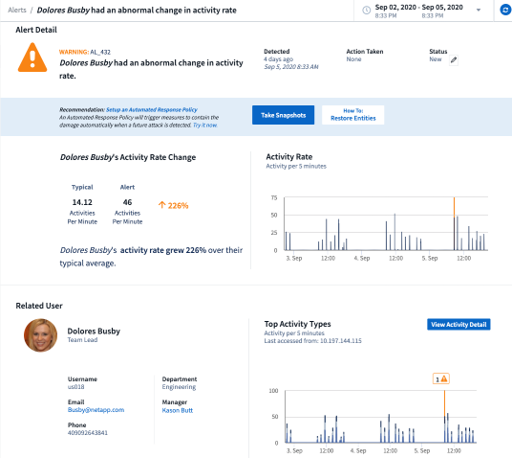
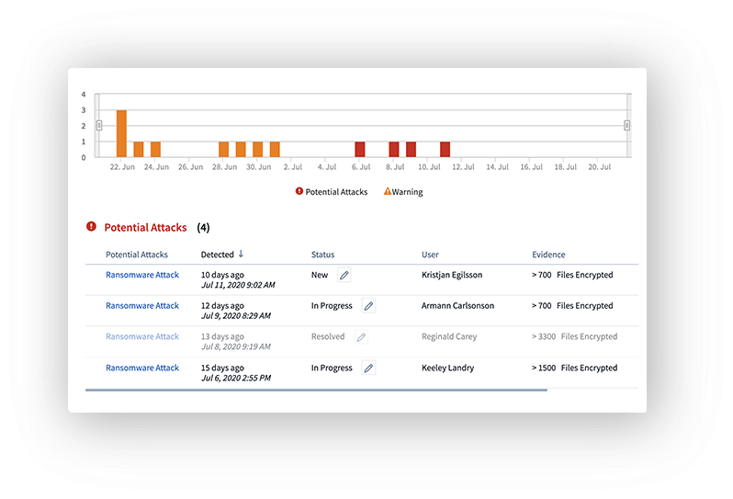
Today’s ransomware and malware are very complex. They use random extensions and file names, which makes it impossible for signature-based (blocklist) solutions to detect them. The advanced machine learning algorithms of Cloud Secure detect potential attacks and unusual data activity. This method provides a dynamic and accurate detection and reduces errors detect noise.
• Automatic Response Policy
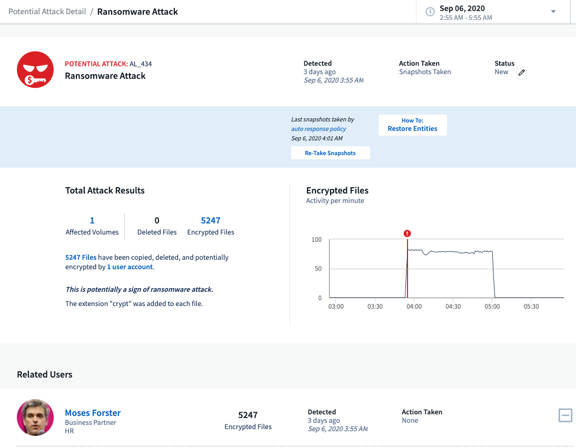
When Cloud Secure detects abnormal behavior, it will alert you and automatically takes a snapshot of the data in order to quickly recover.
• Forensics and user audit reports
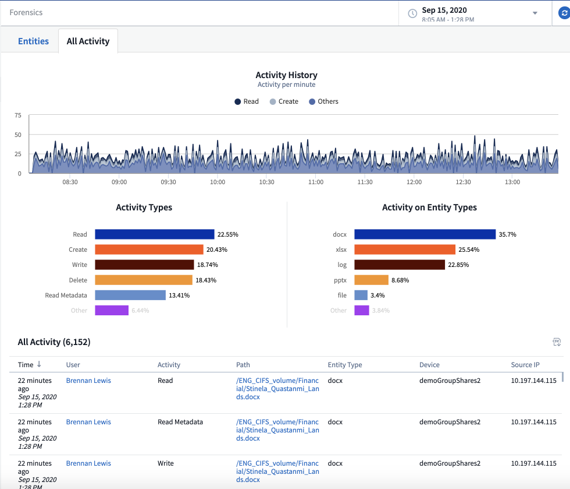
Cloud Secure provides a graphical interface to slice and dice activity data. It performs data leakage investigations and generates user data access to audit reports. It allows users by event type, time, and a plurality of file attributes to view file data activity.
These functions can easily generate user data access, conduct data leakage audit reports, and conduct security incident investigations. Data is stored for 13 months to continue forensic analysis.
NetApp ONTAP

ONTAP® is the industry-leading enterprise data management software for NetApp storage.
ONTAP® helps you create a smart, powerful, and trusted storage infrastructure that reduces costs accelerate critical workloads, and protects and secures data across your hybrid cloud.
NetApp ONTAP®
- Set an alert for the abnormal storage indicators. For example, Data growth, loss of efficiency, or snapshot retention, to identify possible infection.
- Use NetApp FPolicy to approve or exclude file extensions
- Allowing only authorized file extensions.
- Using Smart FPolicy zero trust engine audit logging.
ONTAP Native Tools for Detecting Ransomware
Compared with normal user file creation and modification, ONTAP administrators can more easily discover typical ransomware behavior.
ONTAP storage virtual machine (SVM) may contain encrypted user files, which are placed by the ransomware that running on the client machines, though ONTAP software is not infected with ransomware. The client machines can use SMB / CIFS share or NFS mounted the exported file to access these networks. Since the file is encrypted, this activity looks like a new ONTAP writes to the file system. The original pre-encrypted data will still exist in the file system in the form of NetApp Snapshot ™ copies. Updates only the active file system pointer to reference the encrypted file.
A large change in Snapshot size to detect ransomware attacks
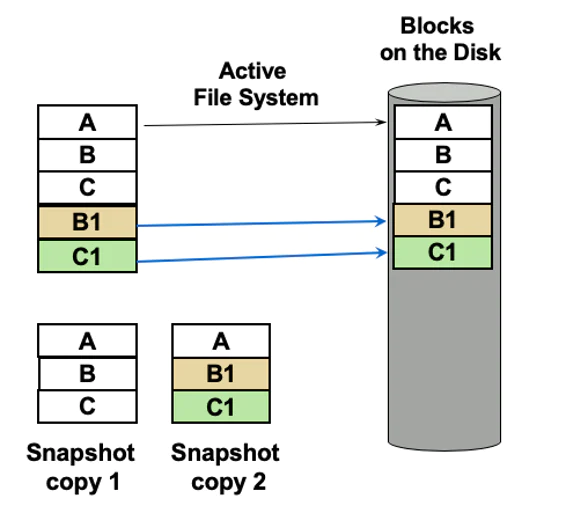
For example in the NetApp WAFL® file system: Blocks A, B, and C represent the original unencrypted file, blocks B1 and C1 represent encrypted file changes. The active file system pointer is updated to reference only the blocks A, B1, and C1, but the original blocks B and C are still present in the Snapshot copy (Snapshot copy 1).
Snapshot copy 2 which is referenced by blocks B1 and C1, is will now contain encrypted files. Due to the new write encrypted by the ransomware, the size of the Snapshot copy 2 will be much larger than Snapshot copy 1. This is an obvious aberrant of the size and percentage change of the Snapshot copy that we can view in ONTAP System Manager. This is a good sign that you may be ransomware attacks.
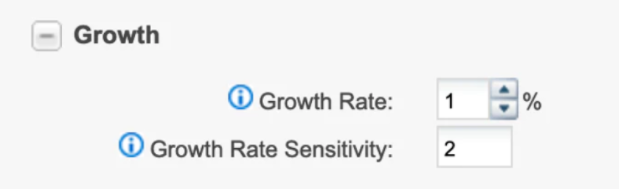
There are two alerts that in NetApp Active IQ® Unified Manager can also be used to detect ransomware. When a volume’s growth rate is abnormal (greater than 1% by default) or the Snapshot reserve used percentage reaches a certain threshold (90% by default), the system will send an alert automatically. The following are examples of these volumes operating condition threshold and the default settings.
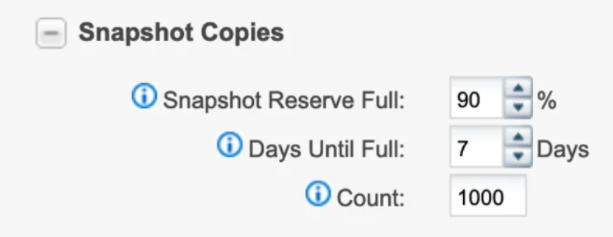
Using storage efficiency measurements to detect ransomware attacks
Storage efficiency dropped significantly also a good sign to detect a potential ransomware attack. The space-saving features of storage efficiency involve compression and deduplication. The compression process involves finding similar data patterns, and that these patterns are not always able to find in encrypted data. Seemingly random encrypted data, compression algorithms almost no recognizable pattern recognition. Likewise, encryption can also affect the efficiency of data deduplication. Deduplication is found common blocks in a file and stored only one duplicate block. It eliminates redundancy and saves a lot of storage space. When there is a potential ransomware attack, similar blocks are not recognized between the files by ONTAP, because it can not read the encrypted block.
Therefore, when the host data encryption, deduplication, and compression are stored. The Storage efficiency is very low.
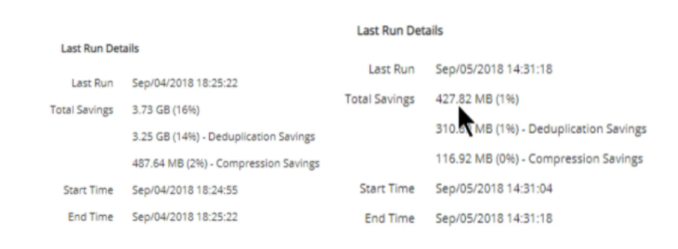
From the before and after of the example, the deduplication percentage dropped from 16% to 1%, and the compression ratio dropped from 2% to 0. These changes can clearly indicate that ransomware attacks may be occurring.
NetApp® FPolicy™
NetApp’s Zero Trust Engine
Blocking engine for known Ransomware file extensions
Security Information and Event Management (SIEM) integration
Anti-Virus and data-security integration
NetApp FPolicy is a file-access notification framework. It may be used to monitor and manage access by the NFS or SMB / CIFS protocol. It is part of ONTAP that helps you detect extortion software. The Zero Trust engines are valuable because you can get extra security measures beyond permissions in the access control list. You can block known ransomware file extensions with FPolicy. Users are still its main folder have full access, but does not allow any file they FPolicy storage administrators marked as blocked. There are two modes of FPolicy operation, which are native mode and external mode.
NetApp® FPolicy™ native mode
Native mode is a build-in ONTAP function, you do not need additional licenses to enable it. It provides the file extension of whitelists and blacklists.
FPolicy Whitelisting
Setting a white list is beneficial if you know exactly the NFS export or SMB / CIFS share on what type of file resides. For example, you should only allow the .ppt extension and block all other files if the only document type you need to store on a particular share is a .ppt file. Encrypted files and change the extension of ransomware then become useless.
FPolicy Blacklisting
Blacklist is what you expect. Not allowing to save on the storage and share if the file with a certain extension. It comes in handy when you know that you are trying to block very specific types of ransomware that use file extensions after completing the encryption process.WannaCry virus is a blacklist of popular extensions. If your environment has begun to erupt, the blacklisting can be rapid hemostasis.
NetApp® FPolicy™ external mode
The external mode has the same functions as the native mode, but it also integrates with the FPolicy server and the security information and event management (SIEM) system running outside the ONTAP system. Therefore, you can get additional features to detect more advanced ransomware. You can use UBA capabilities with the external that could stop even zero-day ransomware attacks and without using extensions.
User Behavioral Analytics (UBA) @ NetApp® FPolicy™ external mode
UBA will track some of our specific access and data processing behavior visits, determine the user’s typical access pattern, and report when the user’s behavior differs from the pattern. Furthermore, if users are doing something beyond their usual pattern, UBA can also deny access to file data. The FPolicy external mode is integrated with an external server, which uses UBA to determine when users are doing things they don’t normally do.
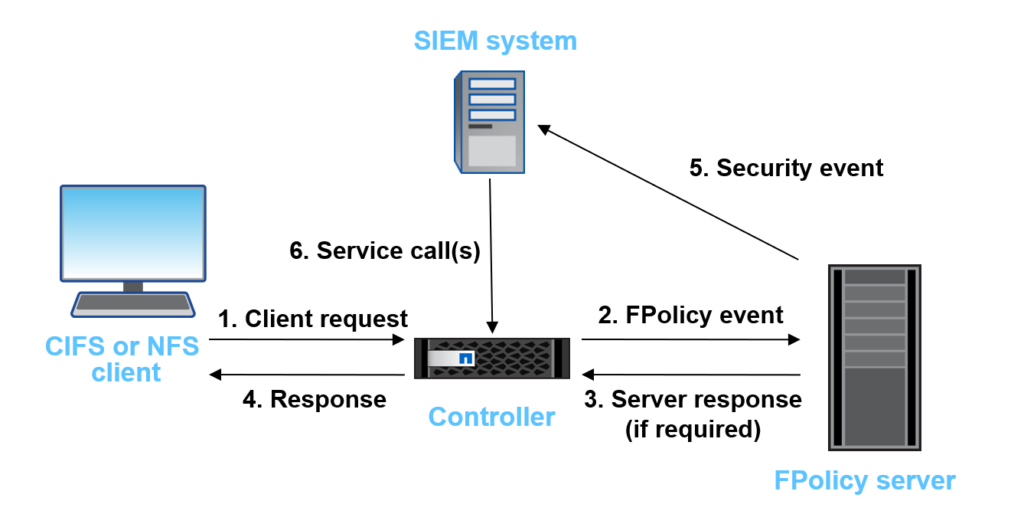
The above figure is an example of a security information and event management (SIEM) system, every CIFS or NFS client request is sent to the FPolicy server, which determines whether access should be allowed.
An example of a security information and event management (SIEM) system, even if users have file permissions on the file data they are trying to manipulate, this additional analysis is performed. Because permissions are difficult to always be correct, UBA with DFPolicy can better measure whether the user is trying to do something evil.
UBA has begun to integrate artificial intelligence (AI) and machine learning (ML) in its external FPolicy server, which shows that it is very powerful. Contact our experts and know more about FPolicy.
Summary
From NetApp Cloud Insights, NetApp ONTAP, and NetApp® Fpolicy™, this blog has already provided the best suggestion on how you can detect ransomware attacks.
In addition, before all the development of prevention programs, you may already be attacked. Therefore the next blog would be focusing on protecting data when the ransomware attack has occurred. If you need a quick start or find out more about ATech ransomware solutions, please click here.
About ATech Communication (HK ) Limited
Ahead of Technology and Communication
We are a leading IT service provider in HK. Focused on business needs, providing solutions, and getting the best return on investment. We are committed to providing cutting-edge IT technologies in order to meet growing customer demand. With the IT infrastructure and application expertise to solve programs, we provide insight and solutions to practical problems before customers face problems. Please visit our Cases page to learn more about our successful works. For more information on ATech, please contact us at enquiry@atechcom.net.
Read More:
What is Ransomware and Why you can’t prevent it?
Ransomware FAQ
Ransomware is malicious software that encrypts the info of targeted victims. The attacker then tried to urge the victim to pay the ransom to get the key to decrypt the file.
Ransomware may be a multi-stage attack packaged by attackers in many various ways. the essential principles are usually equivalent. Infiltrate the target network, encrypt the maximum amount of data possible, and demand ransom. They are:
1. Infection
2. Secure Key Exchange
3. Encryption
4. Blackmail
5. Unlock and restore
- Identify the user file access patterns
- Identify possible end-user accounts become ransomware attack victims before the attacks intensified
- Detecting user exception
Cloud Secure performs 4 main functions:
- Monitor user activity
- Detect anomalies and identify potential attacks.
- Automatic Response Policy
- Forensics and user audit reports
ONTAP® is the industry-leading enterprise data management software for NetApp storage.
ONTAP® helps you create a smart, powerful, and trusted storage infrastructure that reduces costs accelerate critical workloads, and protects and secures data across your hybrid cloud.
- Set an alert for the abnormal storage indicators. For example, Data growth, loss of efficiency, or snapshot retention, to identify possible infection.
- Use NetApp FPolicy to approve or exclude file extensions
- Allowing only authorized file extensions.
- Using Smart FPolicy zero trust engine audit logging.
- NetApp’s Zero Trust Engine
- Blocking engine for known Ransomware file extensions
- Security Information and Event Management (SIEM) integration
- Anti-Virus and data-security integration

ATech Communication (HK) Limited
Providing a Complete Suite of IT Solutions
- (852) 2970 6010 / 3756 0078
- enquiry@atechcom.net


