Cortex XDR for endpoint detection and response
- Thwart sophisticated threats with industry-leading endpoint protection.
- Employ machine learning and analytics to automatically identify covert attacks.
- Expedite investigations by 88% through comprehensive root cause analysis and consolidated alerts.
The majority of endpoint security solutions fall short in delivering the necessary protection and detection features to effectively counter sophisticated threats.

Cortex XDR Feature Highlights
Building Blocks of an Effective Endpoint Security Solution
(1) Advanced Threat Prevention
WHY – Conventional antivirus solutions, which depend on signature databases and updates, struggle to keep pace with the escalating number of new threats. It’s crucial for advanced solutions to help you stay one step ahead of the ever-evolving threat landscape.
HOW – Prevent exploits by focusing on techniques, block malicious files using machine learning, and scrutinize multiple behaviors to halt harmful activities.
It’s estimated that every day sees the registration of 450,000 new instances of malware.
Grasping the Quality of Detection
Evaluating the kinds of threats detected and the technology and methods employed for detection is vital. This evaluation aids your SOC teams in gaining a deeper understanding of the technical context and the behavior of adversaries, enabling them to respond quickly and appropriately.
Refer to independent tests like the MITRE ATT&CK Evaluations to aid in assessing detection coverage.
(2) Superior Detection Capabilities
WHY – Effective threat detection is crucial for a comprehensive defense strategy against complex and potentially harmful threats.
51% of IT professionals attribute the success of endpoint attacks to the inadequacy of their endpoint security solutions in detecting threats.
HOW – Optimal threat detection and response at the endpoint involve rich data collection, advanced query functions for threat hunting, and sophisticated response functions. The use of data analytics techniques, such as machine learning behavioral models, derived from top-tier threat intelligence sources, should feed not only your detectors but also your automated prevention capabilities.
(3) Simplified Investigation & Response
WHY – Intricate systems can result in lengthy investigations and delayed response times.
HOW – Efficient EDR solutions can incorporate methods for threat identification and response, such as causality analysis and risk scoring. Pairing these methods with automation can simplify investigations and decrease response times, providing a comprehensive view with detailed investigative information.
17% of alerts, regardless of their severity, remain uninvestigated, with false positives also contributing to the number of disregarded alerts.
(4) Simplified Deployment & Management
WHY – Fragmented tools compel analysts to switch between consoles to investigate incidents, leading to slow investigations and overlooked attacks.
HOW – Effective EDR solutions enable you to optimize productivity through a platform that encompasses endpoint policy management, detection, investigation, and response in a single management console.
73% of IT operations consider the maintenance of endpoint OS and application versions to be the most challenging endpoint configuration management task.
(5) Industry Validation & Independent Testing
WHY – Real-world third-party testing and a proven track record are dependable indicators of the best EDR solutions in the market.
HOW – Look for solutions that are highly rated, with demonstrated performance through third-party testing, analyst validation, and customer testimonials. You can also request a demo or production environment to test for interoperability, integration, and organizational fit.
“XDR” enhances detection and response, taking them to a new level
- Existing tools are challenging to operate together, hindering immediate attack blocking and response coordination.
- Traditional methods like SOC and SIEM have limitations in achieving precise and effective integration.
- A new approach, XDR, is needed to address current security operation challenges.
- XDR simplifies and accelerates security operations, including threat detection, classification, investigation, and response.
- XDR employs effective threat defense measures to prevent all threats.
- It utilizes AI and machine learning for detecting sophisticated, hidden attack methods.
- XDR uses automation to speed up investigations.
- It operates across multiple data environments for comprehensive security.
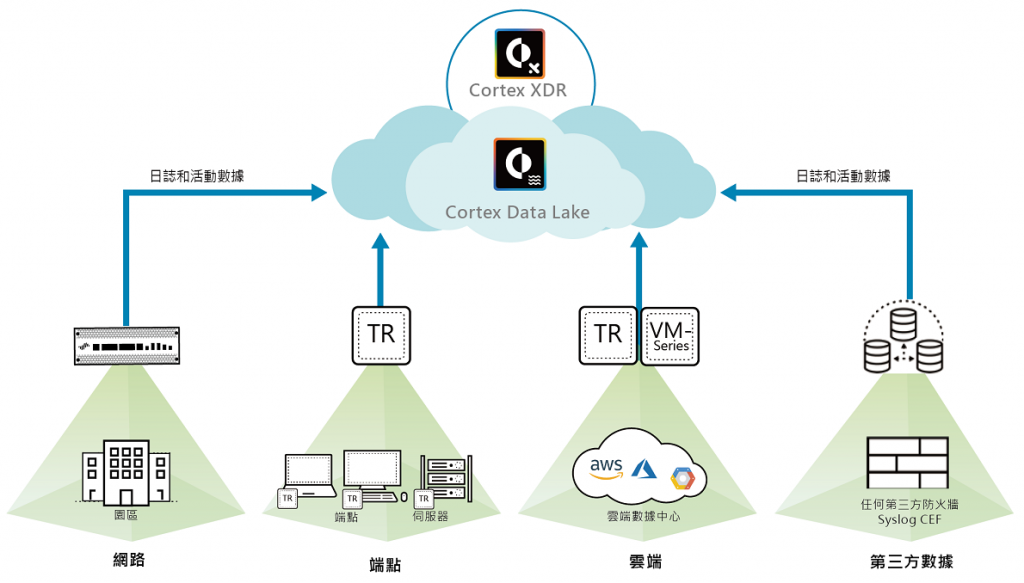
Defend endpoints with a robust endpoint protection solution
Cortex XDR by Palo Alto Networks enhances endpoint security with top-notch prevention, detection, and response to halt complex threats.
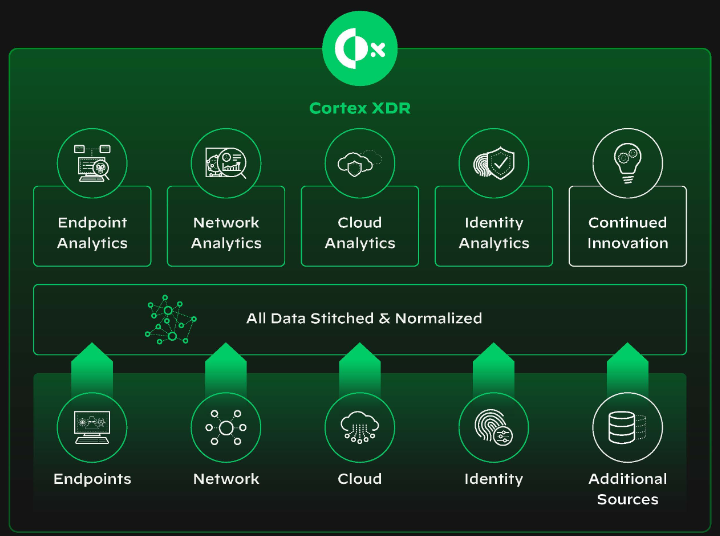
Cortex XDR actively enhances threat detection and response by:
Comprehensive visibility across various platforms.
Analytics and automation for threat analysis.
Streamlines security operations to reduce response time.
Enhances efficiency and reduces costs by consolidating tools.
Lower the Total Cost of Ownership for Detection and Response with Cortex XDR™
To combat growing cybersecurity threats, businesses should invest in Cortex XDR™. It defends against attackers swiftly, eliminating the need for multiple isolated tools. Cortex XDR™ not only prevents complex attacks and reduces costs but also avoids network sprawl.
By integrating detection and response products into one platform, Cortex XDR™ moves data management to the cloud and cuts log management costs, saving 44% of the total ownership cost. It’s a key tool for enhancing security and maximizing operational efficiency.
Learn more about Cortex XDR: https://www.paloaltonetworks.com/cortex/endpoint-detection-and-responsehttps://www.broadcom.com/products/cybersecurity/endpoint/end-user
Read more about Cortex XDR – Security teams are challenged by response times: https://seminar.ithome.com.tw/live/cortexxdr/index.html
About ATech Communication (HK) Limited
ATech Communication (HK) Ltd is one of the leading IT equipment & service provides for HKSAR Government Departments and Bureaux. We provide the best value and the best IT solution to our customers. Please visit our Cases page to learn more about our successful works. For more information on ATech, please contact us at enquiry@atechcom.net.

ATech Communication (HK) Limited
Providing a Complete Suite of IT Solutions
- (852) 2970 6010 / 3756 0078
- enquiry@atechcom.net



