With cyber threats becoming increasingly sophisticated, organizations need robust solutions to protect their applications. That’s where Palo Alto’s Turnkey DevOps Security Solution comes in. Prisma Cloud, offers a powerful combination to fortify your application security.
DevOps Modernization Introduce New Challenges and Risks
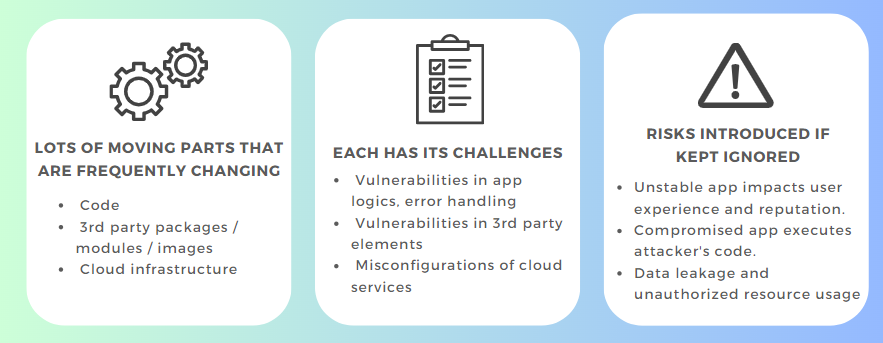
The Snowball Effect
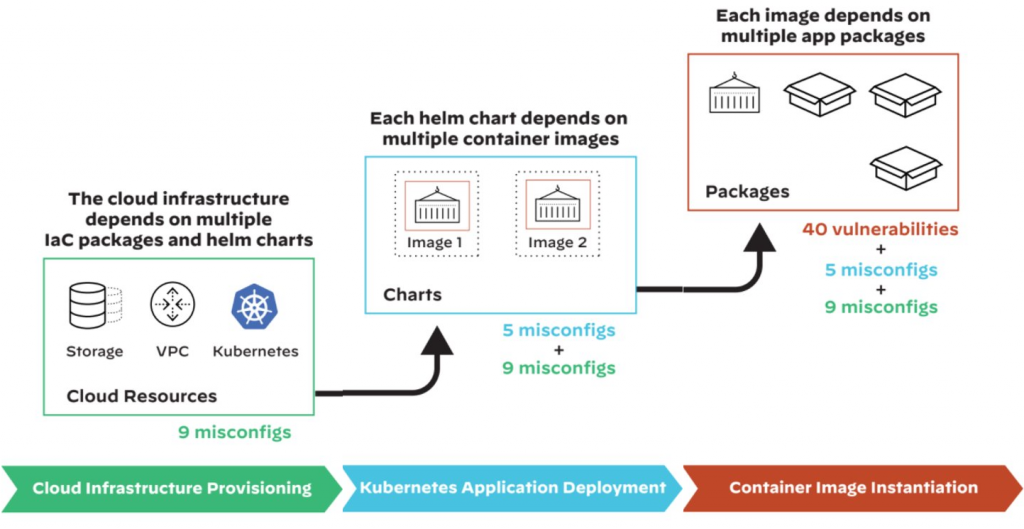
At each stage, different dependent packages are deployed, and various security issues can be subsequently introduced.
- Cloud infrastructure provisioning: The IaC uses three types of Terraform modules: VPC, Kubernetes, and storage. The storage module also depends on two other modules. After all five modules are deployed, a total of nine misconfigurations are introduced.
- Kubernetes application deployment: A Kubernetes application is deployed using a Helm chart. This main Helm chart depends on two other Helm charts, and each Helm chart also depends on two container images. After all three Helm charts are deployed, a total of five Kubernetes misconfigurations are introduced.
- Container image instantiation: Each container image is instantiated to one or more containers across the cluster. Inside each container, the application code and all its dependent packages are loaded into memory. After all eight containers are deployed, a total of 40 application vulnerabilities are introduced.
- This example highlights how vulnerabilities and misconfigurations can quickly snowball within the context of supply chain dependencies. Although the deployed infrastructure in the examples will be fully functional, the default configurations of the dependent packages may not be secure. If any of the dependent packages are compromised, millions of cloud environments relying on them could become vulnerable to attacks like those in recent history.
Risk presents itself across cloud environments and applications

At Palo Alto Networks, we are proud to have a dedicated team of threat researchers called Unit 42 that is exclusively focused on identifying threats and risks across the cloud attack surface. Their research is released bi-annually in what we call our Cloud Threat Report. In this slide, we’ve chosen data points that highlight the variety of risks that organizations face across all the various layers of their cloud environments and applications:
- Compliance, especially for cloud data, is a major risk: According to Unit 42, 43% of cloud databases are not encrypted. This risk speaks to the data concerns that you have when you start using cloud services. Importantly, organizations need to ensure that they have configured data storage correctly and misconfigurations of those services are addressed.
- Vulnerabilities in applications need to be addressed: Whether you are using typical cloud virtual machines, containers, or serverless functions, you need to continuously monitor them for vulnerabilities. This is evident in the data point that 91% of all container images have at least one critical or high severity vulnerability.
- Insecure network configurations and communications can leave your data and applications exposed: According to Unit 42, 60% of organizations have insecure network configurations. As applications continue to operate across multi- and hybrid-cloud environments, securing networks becomes essential.
- Identity and entitlement risks are paramount: Security and identity teams need to be able to address cloud infrastructure entitlements in order to remove over-permissioned entitlements, while also ensuring least-privileges. Unit 42 highlights this concern — 66% of organizations worldwide are using access keys for longer than 90 days.
Ultimately, these risks are not meant to scare security teams, but paint a picture of the comprehensive security requirements in today’s multi-cloud world.
Sources: Various. Latest Cloud Threat Report here.
Prisma Cloud Benefits:
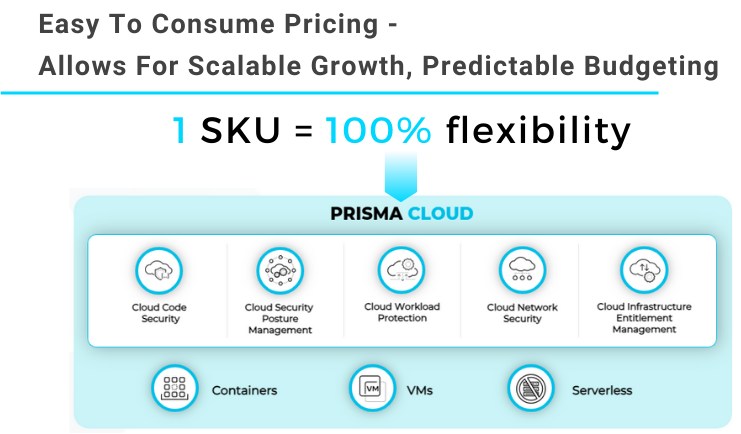
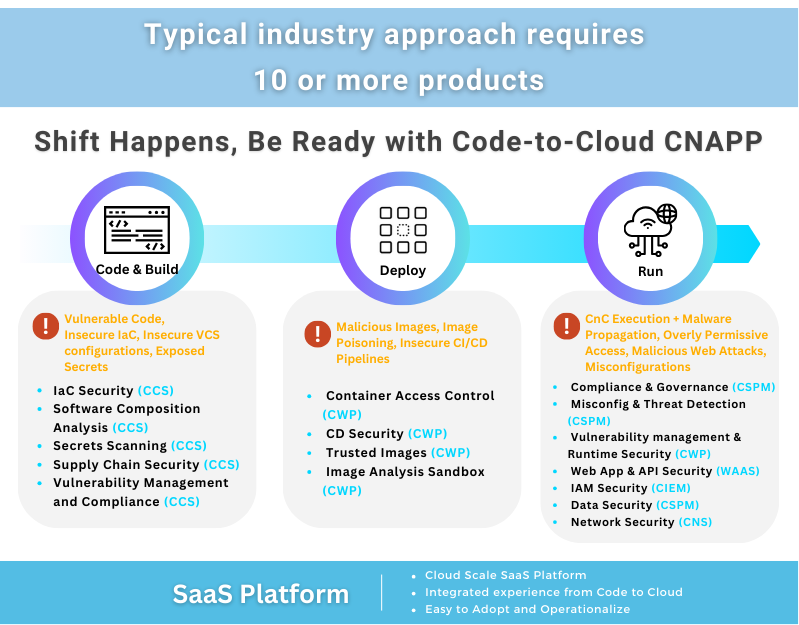
One of the current dynamics that we aim to address with Prisma Cloud is the growing number of security tools used by today’s enterprises. According to the 2020 State of Cloud Native Security Report, 60% of respondents shared that they were using more than 6 cloud security tools. Gartner estimates that organizations are manually stitching together “10 or more disparate security tools”.
Using this significant number of point solutions adds challenges and gaps for security teams, including:
- An incomplete picture of risk: If you have multiple tools across the application pipeline and at runtime, for example, a CSPM tool, a standalone vulnerability management tool, multiple runtime protection tools for different tech stacks, and a WAF, you lack a centralized view of risk across your environment.
- Multiple consoles lead to increased complexity: If cloud infrastructure and security teams are constantly switching between consoles, they are spending precious time and resources comparing results and data, rather than addressing security issues or managing risk.
- Lack of centralized policies that create added overhead: Organizations using open source tools or point solutions spend a significant amount of time creating policies and correlating policies between vendors and tooling. By using a centralized platform, teams can use centralized policies maintained by our industry-leading product team.
With our approach to Cloud Native Application Protection Platforms, organizations can centralize security to a single solution to achieve powerful business outcomes and ROI, which we will discuss today.
Learn more about Prisma Cloud: https://www.paloaltonetworks.com/prisma/cloud
Read more about Cloud Security Platform : https://www.paloaltonetworks.com/prisma/cloud/cloud-security-platform
About ATech Communication (HK) Limited
ATech Communication (HK) Ltd is one of the leading IT equipment & service provides for HKSAR Government Departments and Bureaux. We provide the best value and the best IT solution to our customers. Please visit our Cases page to learn more about our successful works. For more information on ATech, please contact us at enquiry@atechcom.net.

ATech Communication (HK) Limited
Providing a Complete Suite of IT Solutions
- (852) 2970 6010 / 3756 0078
- enquiry@atechcom.net



