Ransomware Protection: How would NetApp provide protection after ransomware being detected
Ransomware is certainly not something new to you and your organization. You must have recognized the increased risk of ransomware attacks and how terrifying ransomware is. Nevertheless, not a few IT specialists are still underestimating themselves in keeping their organization safe from ransomware, or they are simply clueless about what they could do.
Read More:
What is Ransomware and Why you can’t prevent it?
Indeed, ransomware is hazardous enough not only to paralyze the operation of your organization for a while. Instead, it is powerful enough to force you to surrender your power of data protection completely and put your organization into a huge crisis for leakage of your clients’ private information. You might have understood that even a paid pro version of antivirus is nowhere good enough to distant your organization from ransomware, but in fact, you need not consider ransomware to be a demon that you would keep praying to hide from. Ransomware protection technology does exist nowadays to keep you safe from being ‘cursed’ by ransomware. NetApp, especially its flagship ONTAP® data management software, has been doing great in this area.
For more information, visit the NetApp ONTAP website
You managed to know from our last blog that how NetApp works in detecting ransomware, and in case your organization was notified to have become a victim of a ransomware attack, you could rest assured that it is never an announcement of the doom day of your organization. You are going to know more about the mechanism and technology of the ransomware protection offered by NetApp. Here comes the second stage – Protect.
Read More:
Ransomware Protection: NetApp Snapshot Technology provides rapid back and recovery
IT specialists of organizations always aim to create an environment for each function to operate independently according to a proper workflow, with minimal but necessary infrastructure control. The commonest focus of them is defense. They keep striving to block staff members from using unauthorized software, external devices and restrict the individuals’ access to the internet. They also put much effort into tackling viruses and building strong firewalls. Nevertheless, they tend to choose hiding instead of fighting when setting strategies to deal with ransomware, hence most of them might not have in-depth knowledge of storage systems and backup software.
Ransomware ‘kidnap’ the system by penetrating into its database and encrypting the files, asking for a ransom to offer decryption keys. Traditional ways of ransomware protection count on backup and restore technologies, which are based on streaming data protection devices, such as tape or streaming disk devices that emulate tape. These technologies might be capable of ingesting a large amount of data, but restoring and retrieving data would be complicated and time-consuming enough to reveal their slow response and resource-intensiveness. Being the first company shipping high-volume open systems and “point-in-time” snapshot capability, NetApp Snapshot technology delivers more stability, scalability, recoverability, and performance than competing snapshot technologies.
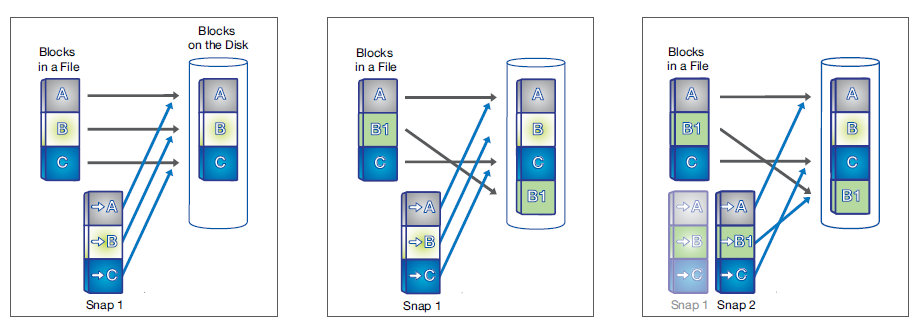
NetApp Snapshot technology makes instant copies, up to 1023 Snapshot copies per volume, of your valuable data while applications run. A Snapshot copy is a point-in-time file system image. Low-overhead Snapshot copies are made possible by the unique features of the WAFL® (Write Anywhere File Layout) storage virtualization technology that is part of Data ONTAP®. WAFL uses pointers to the actual data blocks on disk with not rewriting existing blocks. It writes updated data to a new block and changes the pointer. A NetApp Snapshot copy simply manipulates block pointers, creating a “frozen” read-only view of a WAFL volume that lets applications access older versions of files, directory hierarchies, and/or LUNs (logical unit numbers) without special programming. Snapshot copies are exceptionally efficient both in the time needed to create them and in storage space because actual data blocks aren’t copied.
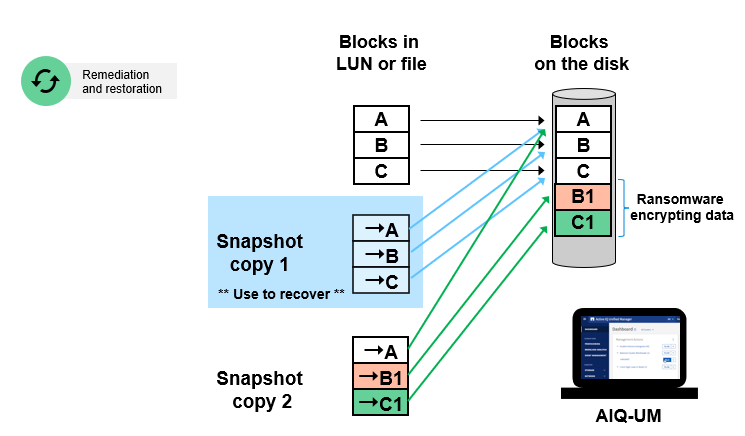
Regardless of the size of the volume or the level of activity on the NetApp storage system, a NetApp Snapshot copy takes only a few seconds or even less than a second to create. Users can comfortably store up to 1023 Snapshot copies per WAFL volume, all of which are accessible as read-only and online versions of the data. Moreover, hundreds of TBs of files could be restored in only a few seconds. Snapshot technology simply possesses competitive edges in stability, performance, scalability, efficient store utilization, user visibility, and file recoverability.
Ransomware Protection: NetApp SnapCenter simplifies backup, restore, and clone lifecycle management with application-integrated workflows
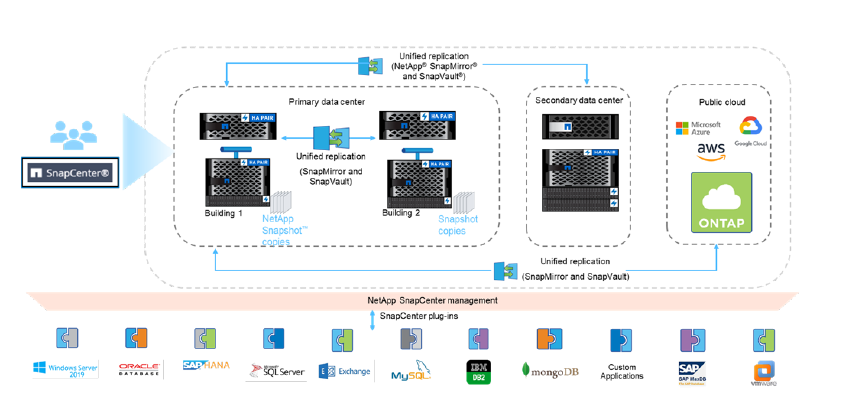
After tons of Snapshot copies are created with the highly efficient Snapshot technology, the stage is reserved for NetApp SnapCenter to shine. This software is a simple, unified platform for application-consistent data protection and clone management, simplifying backup, restore, and clone lifecycle management with application-integrated workflows.
NetApp SnapCenter includes both the SnapCenter Server and individual lightweight application, database, and operating system plug-ins that are all controlled from a central management console delivering a consistent user experience across all applications or databases. It supports critical functions like job monitoring, event notification, logging, dashboard, reporting, scheduling, and policy management for all application or database plug-ins. SnapCenter Server includes Snapshot catalog management to facilitate easy rollback to point-intime copies. It checks the application, database, and OS interoperability and then non-disruptively installs and upgrades software plug-ins on application and database hosts, which can be managed from the central management console.
While the onboard capabilities of NetApp ONTAP storage-based Snapshot technology decide the backup and restore performance, SnapCenter is designed to offload this functionality and deliver high-performance backup and recovery for database and application workloads hosted on ONTAP storage. By leveraging the embedded functionality of NetApp ONTAP storage software to perform space-efficient NetApp FlexClone management, SnapCenter enables greater agility by increasing the performance of testing and development. Application and database administrators can initiate FlexClone volumes independent of storage administrators through the same GUI console to support highly iterative test and development workflows. The testing and development time is thus reduced by the self-service feature of space-efficient cloning. SnapCenter uses RBAC to delegate functionality to application and database owners while retaining oversight and control by a central storage infrastructure administrator. Not only do storage administrators benefit from this level of control and security, but such control also protects the overall infrastructure from abuse.
SnapCenter software securely coordinates and manages data protection across applications, databases, and file systems. It tightly integrates with your enterprise applications and delivers the control and choice needed to enable application and database owners to manage their own environment through RBAC while preserving the integrity of the storage environment.
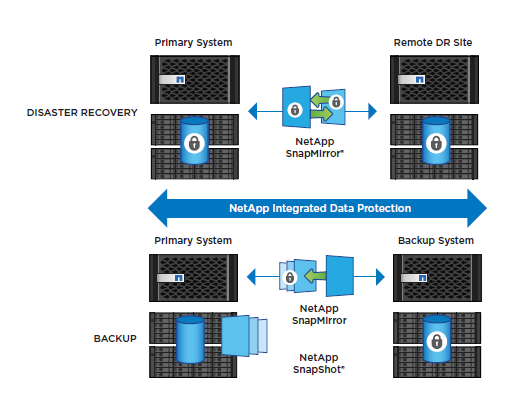
Ransomware Protection: NetApp SnapVault and SnapMirror provides the fastest backup and recovery
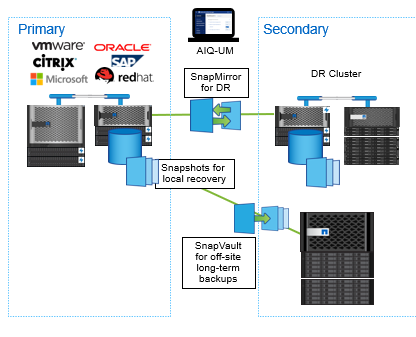
SnapCenter leverages NetApp storage-based backup and replication functions, such as with NetApp SnapVault and SnapMirror technology. SnapVault helps in responding with replication-based disk-to-disk backup. Backups finish in minutes instead of hours or days with SnapVault. Weeks, months, or years of backups can be kept online, all while your disk capacity requirements are reduced up to 90% in virtualized environments. Based on Snapshot point in time copies, each backup is block-level incremental but represents a full backup from a restore perspective. Only the new or changed blocks are added to the secondary backup, bandwidth can be saved and backup storage needs can be reduced. Since the backups are in offline and native format, they can be restored in minutes, unlike dedicated backup appliances that put the data into a proprietary backup format.
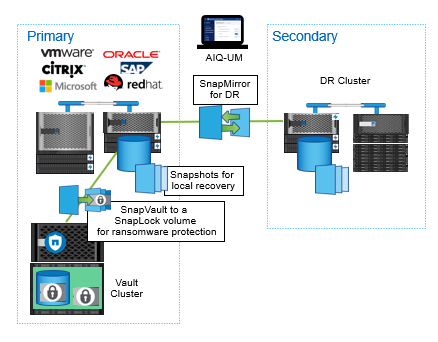
Unlike other solutions, SnapVault copies can also be leveraged for testing, development, e-discovery, and reporting with no impact to your operations—or they can be replicated by using NetApp SnapMirror technology for disaster recovery. While Snapshots are being used for local recovery, SnapMirror keeps communicating with a secondary data center. It turns out to be a cost-effective, easy-to-use unified replication solution across the data fabric for business continuity and disaster recovery purposes. At the same time, SnapVault creates off-site long-term backups which are immutable. The backups can also be made undeletable while they are essentially “air-gapped” in SnapLock Compliance volume.
Ransomware Protection: NetApp SnapLock Compliance software provides WORM immutable storage

Spot the problems and tackle them, then fix all the damaged parts and get the operation resumed to normal. Finally, lessons have to be taken for getting immune to the same problems. This is a common process of how we deal with issues in our lives, while this is also how NetApp works for you on ransomware protection. While the Snapshot technology and SnapCenter rescued your files and saved you from paying the ransom, the SnapLock Compliance software keeps you safe from repeating attacks by making the Snapshots immutable and undeletable.
To comply with strict record retention and performance requirements, organizations worldwide are required to archive emails, documents, patient records, design files, and other data for years. The data has to be even proven not changed or deleted. When ransomware attacks, your failure to quickly retrieve required records could result in financial liability or damage to the reputation of your organization. However, traditional optical disks or tape fail to provide easy and rapid access to data.
NetApp SnapLock software delivers high-performance disk-based data permanence for HDD and SSD deployments. It helps provide data integrity and retention, enabling electronic records to be both unalterable and rapidly accessible. SnapLock also integrates with top archive and enterprise content management (ECM) applications. It includes the ability to address an expanded set of retention requirements, including Legal Hold, Event-Based Retention, and Volume Append Mode (VAM). VAM allows customers to incrementally append files while locked for use cases such as video and audio surveillance and logging.
SnapLock provides fast WORM (Write Once, Read Many) storages which the high-performance, non-rewritable, non-erasable disk storage (SSD or HDD) helps protect data until a specified retention date. It supports disk-to-disk backup and replication of SnapLock volumes, as well as NDMP to tape. Its storage-efficient technology reduces the space required by archives and archive backups by 50% or more.
Read More:
About ATech Communication (HK ) Limited
Ahead of Technology and Communication
ATech is a Leading IT service provider in Hong Kong. We provide the best value, the most widely used system of quality products, customized solutions, and services to strengthen our reputation. ATech is committed to providing total solutions through the expertise we have developed, the talents we have, and the experience we have gained to meet customer expectations. If you’d like to learn more about ATech and the work we’ve done, visit our Cases page. For more information on ATech, please contact us at enquiry@atechcom.net.
Ransomware FAQ
Ransomware is malicious software that encrypts the info of targeted victims. The attacker then tried to urge the victim to pay the ransom to get the key to decrypt the file.
Ransomware may be a multi-stage attack packaged by attackers in many various ways. the essential principles are usually equivalent. Infiltrate the target network, encrypt the maximum amount of data possible, and demand ransom. They are:
1. Infection
2. Secure Key Exchange
3. Encryption
4. Blackmail
5. Unlock and restore
Regardless of the size of the volume or the level of activity on the NetApp storage system, a NetApp Snapshot copy takes only a few seconds or even less than a second to create. Users can comfortably store up to 1023 Snapshot copies per WAFL volume, all of which are accessible as read-only and online versions of the data.
SnapCenter supports a variety of applications and protocols. Consult the NetApp Interoperability Matrix Tool (IMT) for details.
ONTAP® is the industry-leading enterprise data management software for NetApp storage.
ONTAP® helps you create a smart, powerful, and trusted storage infrastructure that reduces costs accelerate critical workloads, and protects and secures data across your hybrid cloud.
NetApp SnapLock software delivers high-performance disk-based data permanence for HDD and SSD deployments. It helps provide data integrity and retention, enabling electronic records to be both unalterable and rapidly accessible. SnapLock also integrates with top archive and enterprise content management (ECM) applications. It includes the ability to address an expanded set of retention requirements, including Legal Hold, Event-Based Retention, and Volume Append Mode (VAM). VAM allows customers to incrementally append files while locked for use cases such as video and audio surveillance and logging.
SnapLock provides fast WORM (Write Once, Read Many) storages which the high-performance, non-rewritable, non-erasable disk storage (SSD or HDD) helps protect data until a specified retention date. It supports disk-to-disk backup and replication of SnapLock volumes, as well as NDMP to tape. Its storage-efficient technology reduces the space required by archives and archive backups by 50% or more.

ATech Communication (HK) Limited
Providing a Complete Suite of IT Solutions
- (852) 2970 6010 / 3756 0078
- enquiry@atechcom.net


